Jimber
Jimber uses a combination of Zero Trust and Isolation Technology to protect companies from hackers and cyberthreats

Jimber uses a combination of Zero Trust and Isolation Technology to protect companies from hackers and cyberthreats
Jimber is a Belgian company created in 2018 by ethical hackers who were not satisfied with traditional cybersecurity tools.
As ethical hackers, they know better than anyone how easy it is to break into these systems and how difficult it is to scale and upgrade them.
That’s why Jimber is constantly looking for innovative approaches to cybersecurity software, and they are constantly challenging their own technology and applications.
Protect your sensitive data and equipment without expensive hardware or performance loss
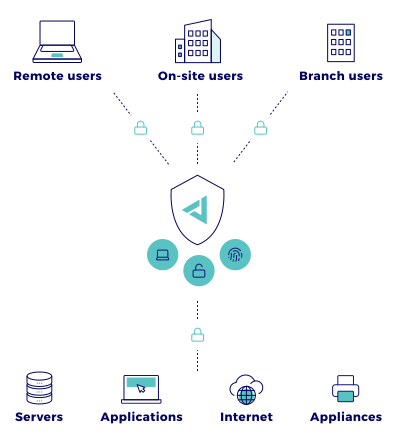
Zero Trust Network Access (ZTNA) is an IT security technology that keeps your company’s network and data safe from hackers and other cyberthreats.
ZTNA takes a “never trust, always verify” approach to network access. It provides secure remote access to corporate applications, data, and services by always enforcing strict identity verification and access controls.
Only authorised users with verified devices can access specific resources on the network. This means that even if a hacker should gain unauthorised access to the network, they will not be able to access sensitive information.
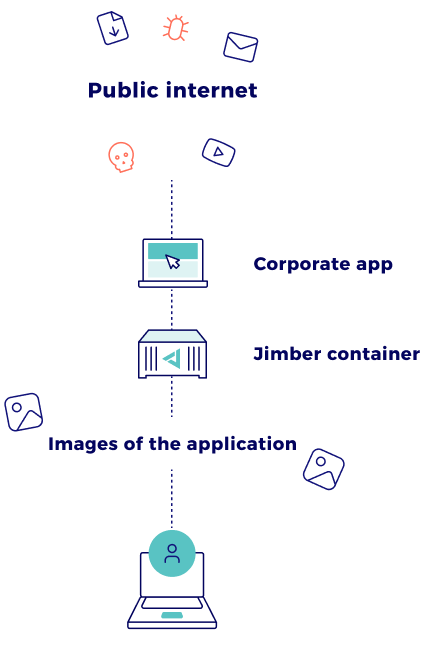
Browser isolation is an extension to our Zero Trust Network Isolation. To protect Internet users and your company’s resources, we add an extra layer of security to each browsing session. We call it a container.
When you visit a website, the code is sent to our container that acts as a sandbox. You won’t interact with the website but with images of the website we send from the container. You’ll get a visual stream of content, just like you’re rendering a video from the internet. The actual web content never reaches your system, so you needn’t worry about injection and related cyberthreats. And the best thing: your experience will stay the same! You can still select text, copy, paste, save, print…
In practice, users won’t notice a thing, but hackers won’t be able to put malware in the code and have your computer execute it.
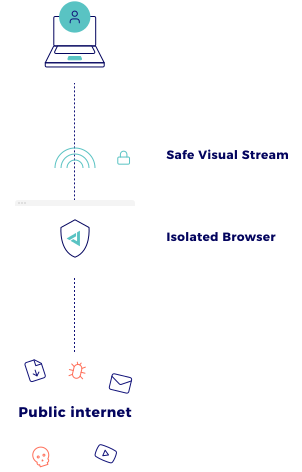
Protect your network against cyber threats with network isolation
Allow safe browsing from any location with browser isolation
Become a FieldTrust partner today and get access to:
| Cookie | Durée | Description |
|---|---|---|
| cookielawinfo-checbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-advertisement | 1 year | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Advertisement". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |
| Cookie | Durée | Description |
|---|---|---|
| YSC | session | This cookies is set by Youtube and is used to track the views of embedded videos. |
| Cookie | Durée | Description |
|---|---|---|
| _ga | 2 years | This cookie is installed by Google Analytics. The cookie is used to calculate visitor, session, campaign data and keep track of site usage for the site's analytics report. The cookies store information anonymously and assign a randomly generated number to identify unique visitors. |
| Cookie | Durée | Description |
|---|---|---|
| ANONCHK | 10 minutes | This cookie is used for storing the session ID for a user. This cookie ensures that clicks from advertisement on the Bing search engine are verified and it is used for reporting purposes and for personalization. |
| IDE | 1 year 24 days | Used by Google DoubleClick and stores information about how the user uses the website and any other advertisement before visiting the website. This is used to present users with ads that are relevant to them according to the user profile. |
| MUID | 1 year 24 days | Used by Microsoft as a unique identifier. The cookie is set by embedded Microsoft scripts. The purpose of this cookie is to synchronize the ID across many different Microsoft domains to enable user tracking. |
| test_cookie | 15 minutes | This cookie is set by doubleclick.net. The purpose of the cookie is to determine if the user's browser supports cookies. |
| VISITOR_INFO1_LIVE | 5 months 27 days | This cookie is set by Youtube. Used to track the information of the embedded YouTube videos on a website. |
| Cookie | Durée | Description |
|---|---|---|
| _clck | 1 year | No description |
| _ga_YHBH8J5EGP | 2 years | No description |
| -YqrHue | 1 day | No description |
| CLID | 1 year | No description |
| CONSENT | 16 years 9 months 16 days 8 hours | No description |
| mdRwtsLBcOfinQ | 1 day | No description |
| SERVERID77446 | No description | |
| SM | session | No description |
| SRM_B | 1 year 24 days | No description |
| TblXvCpGdLNnRxD | 1 day | No description |